Phishing attacks happen every day. Stop, look, think.
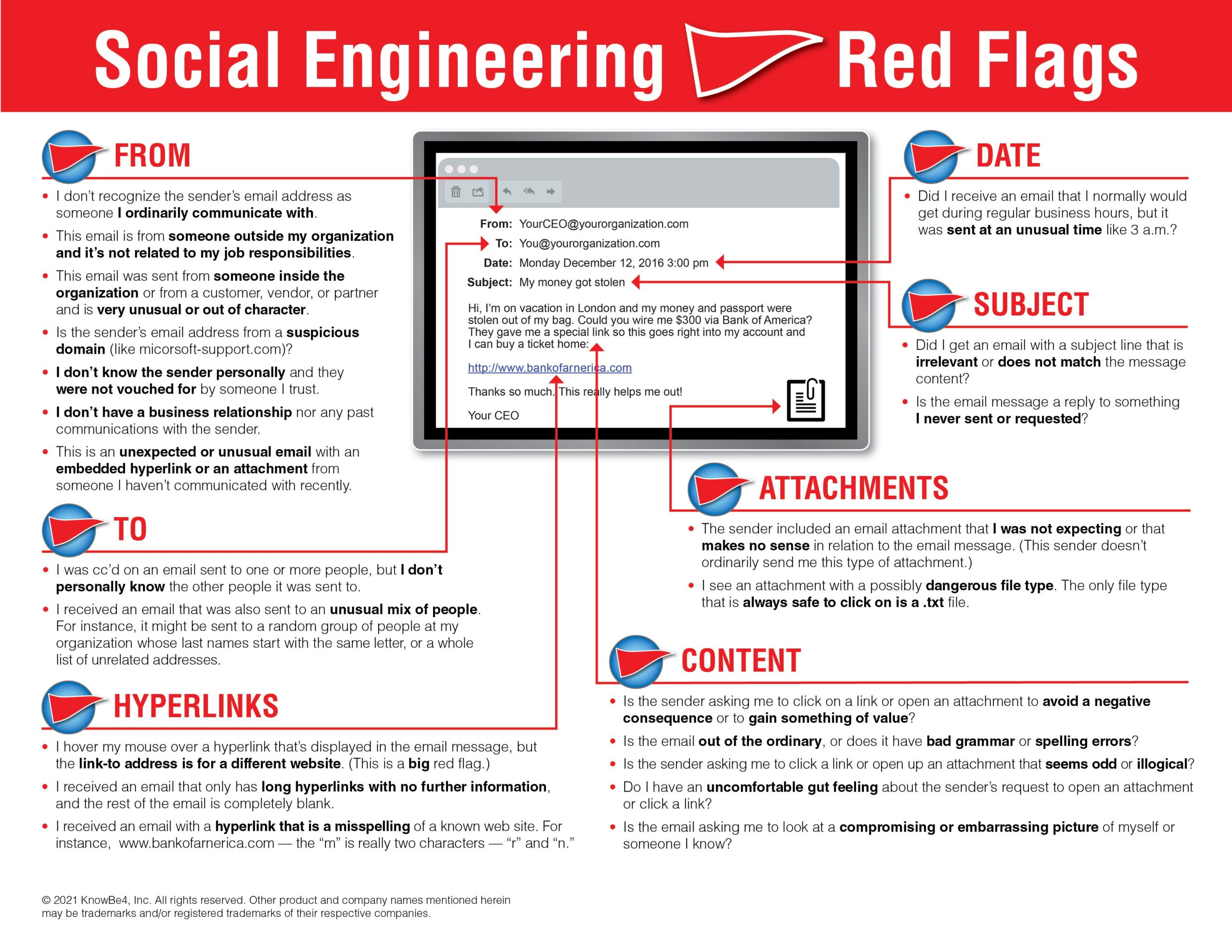
Phishing attacks are not a new concept, but they remain one of the most effective tools in the cybercriminal arsenal. With the growth of digital communication, phishing schemes have evolved and adapted, making it even more critical for users to be cautious and discerning. Understanding the social engineering mechanisms behind these attacks is essential for everyone in today’s digital age.
What are Phishing Attacks?
At its core, phishing is a type of online deception. Cybercriminals use seemingly legitimate messages, usually via email, to trick individuals into revealing sensitive information like passwords, credit card numbers, or bank account details. These messages can mimic those from well-known organizations, such as banks, service providers, or even friends and family.
The Social Engineering Behind Phishing
Social engineering is the art of manipulating individuals to perform actions or divulge confidential information, often by exploiting human psychology. In the case of phishing:
1. Urgency: Many phishing emails create a sense of urgency, pushing the victim to act quickly without thinking. For instance, they might say, “Your account will be locked in 24 hours unless you verify your identity now!”
2. Familiarity: Phishers often use known company logos, familiar email formats, and even spoofed email addresses to make their messages appear genuine.
3. Fear: These scams can prey on fear, suggesting that there’s been suspicious activity on an account or that personal data is at risk.
4. Curiosity or Greed: Some phishing attempts offer too-good-to-be-true deals or claim that you’ve won a prize to lure victims into clicking malicious links.
Stop, Look, Think: A Simple Strategy
To avoid falling victim to phishing attacks, always:
1. Stop: Before you click on any link or provide personal information, pause. Do not let urgency or fear dictate your actions.
2. Look: Examine the message. Check for misspellings, unusual language, or other inconsistencies. Hover over links (without clicking) to see where they lead. Confirm the sender’s email address.
3. Think: Why are you receiving this message? Were you expecting it? If unsure, contact the purported sender directly through a trusted method (like their official website) to verify.
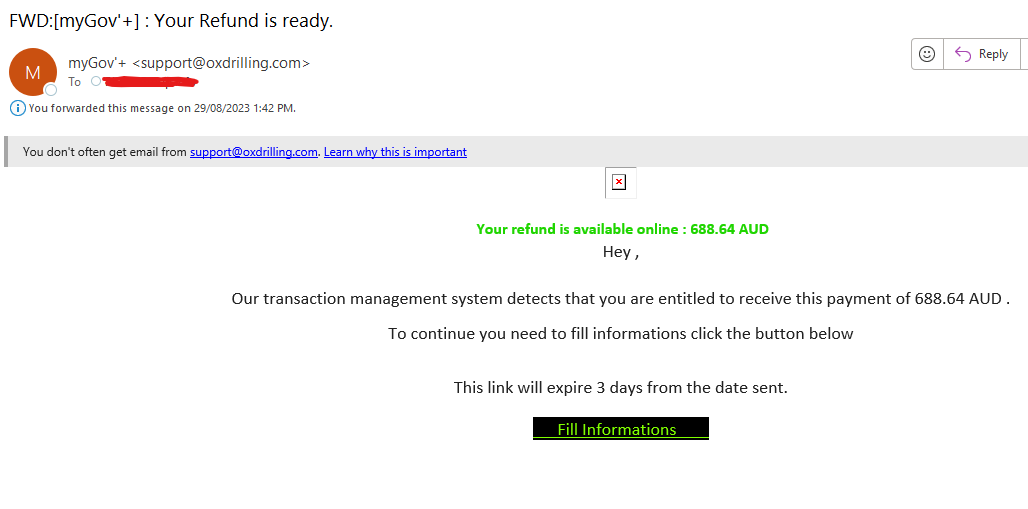
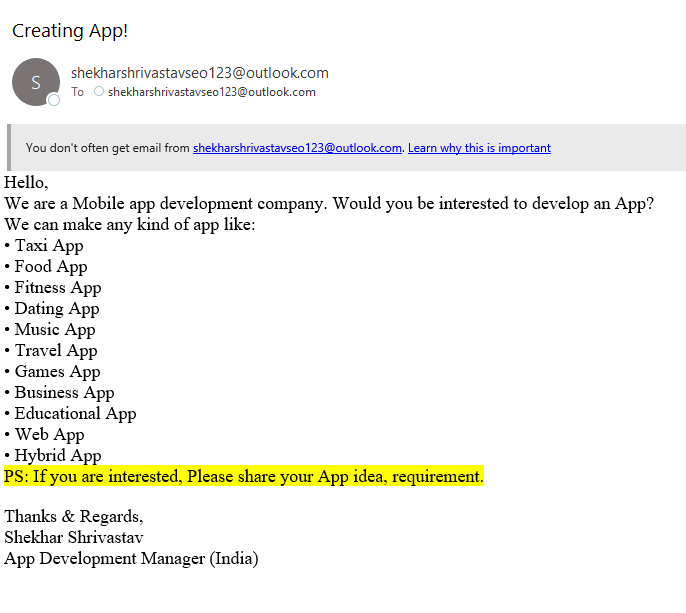
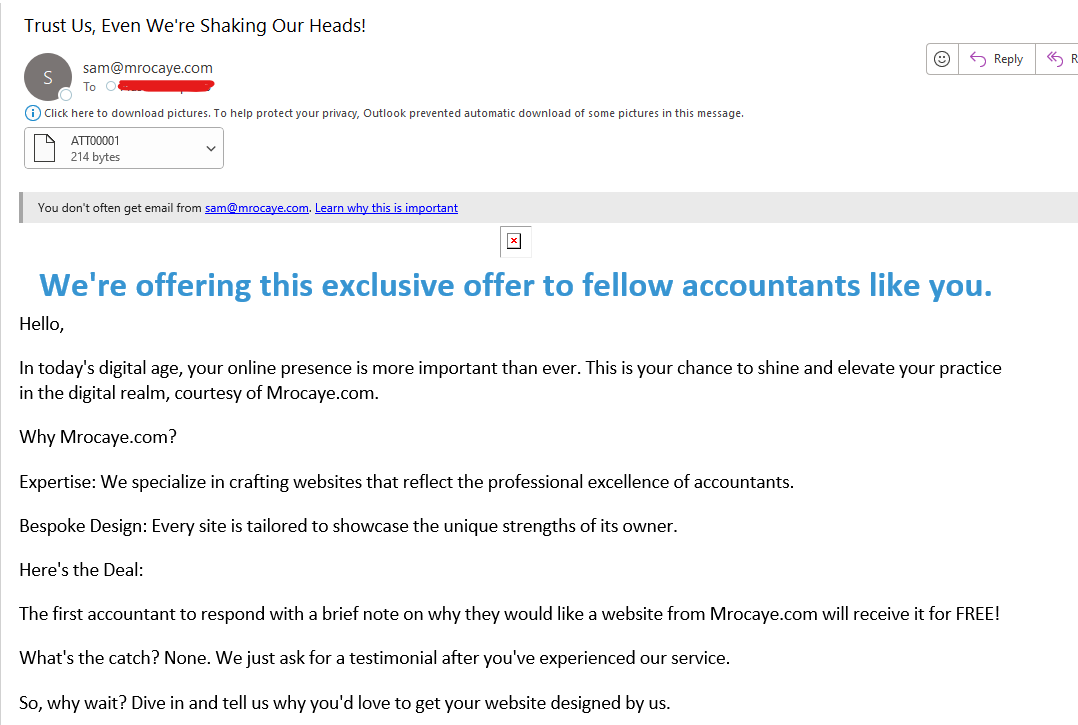
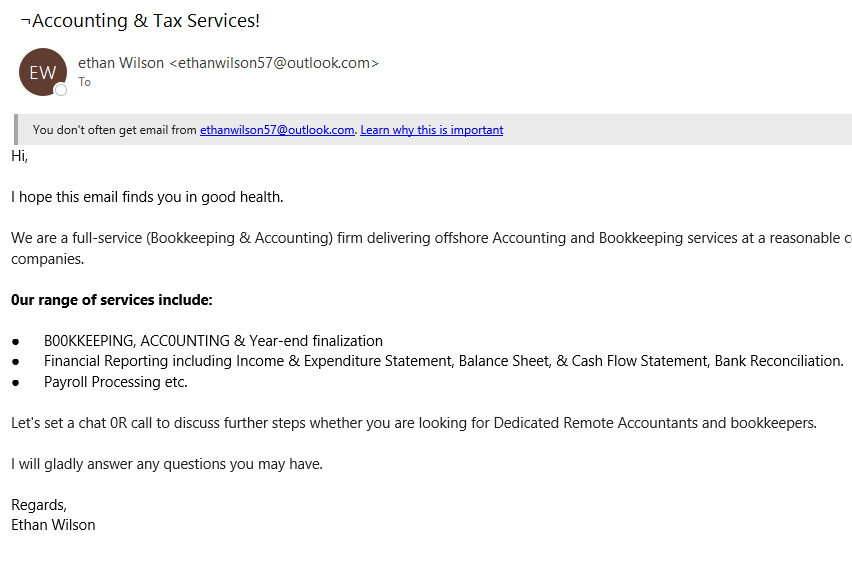
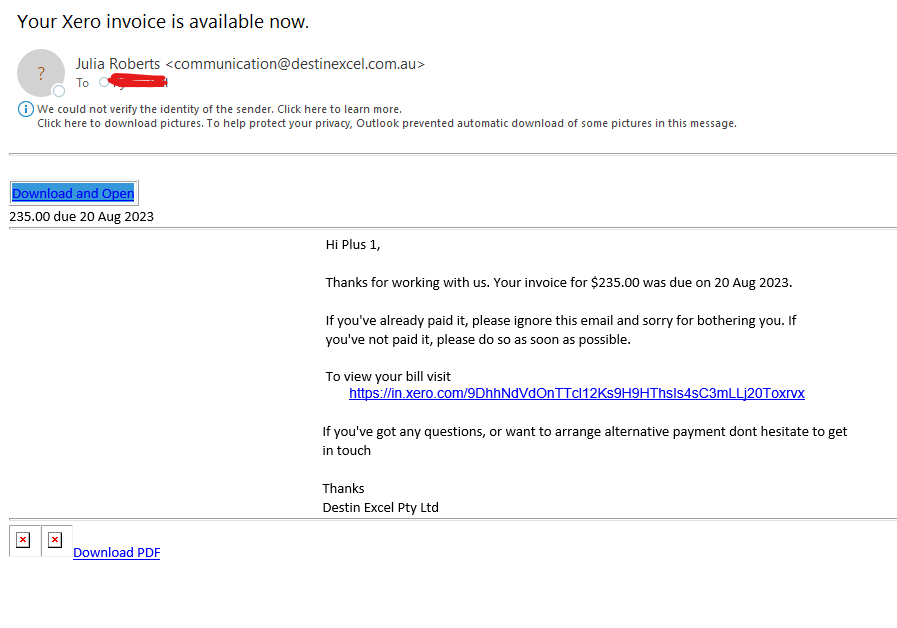
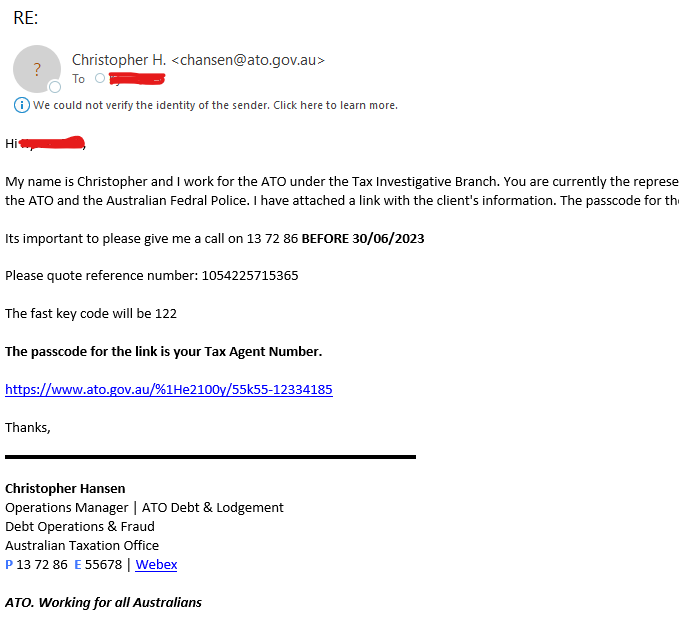
Here are some examples of phishing emails Plus 1 Group gets all the time:

Need more help or information?
Click the link below to contact us at Plus 1.
Open Hours
Monday to Friday
8:00am to 5:00pm
Closed Public Holidays

If you need to get us documents quickly, access remote support, or the MYOB Portal click the button above.


